Man-in-the-middle attack
Updated: 11/13/2018 by Computer Hope
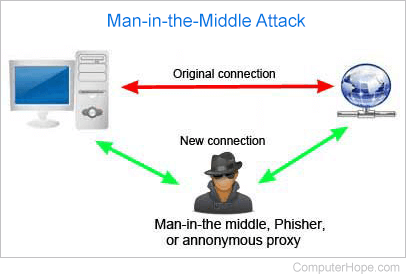
Abbreviated as MITMA, a man-in-the-middle attack is where someone gets between the sender and receiver of information, sniffing any information sent. Sometimes, users may send unencrypted data, which means the MITM (man-in-the-middle) can obtain unencrypted information. In other cases, a user may obtain information from the attack but must decrypt it before it can be read. The picture below is an example of how a man-in-the-middle attack works. The attacker intercepts some or all traffic from the computer, collects the data, and then forwards it to the original destination.
Computer acronyms, Encrypt, Phishing, Security terms, Side jacking, Threat
