Meltdown and Spectre

Meltdown and Spectre are security vulnerabilities that affect most modern CPUs (central processing units). Practical exploits for these vulnerabilities were discovered independently in 2017 by researchers at Graz University of Technology in Austria, and Google's Project Zero in California. The vulnerabilities were announced on January 3, 2018.
Meltdown

Meltdown is a vulnerability specific to Intel CPUs. When Intel CPUs are asked to prefetch data, they read the data before checking the privileges of the user. Although privileged data is not delivered to the unprivileged user, the CPU operates differently based upon the specific data that was fetched. An attacker can monitor the processor's performance in a side-channel and discern important details about the data. This information improves the chance, or in some cases guarantees, that subsequent attacks will succeed.
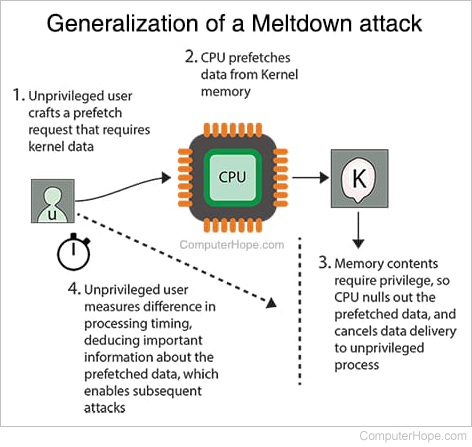
The effect is similar to seeing someone moving something behind a curtain. You cannot see the thing, but if you can see its shape and movement in the curtain, you can make an educated guess about what it is. It's called "Meltdown" because the informational barrier that protects privileged data is effectively dissolved by the attack.
The video below, created by researchers who discovered it, shows a proof-of-concept Meltdown attack in action.
Spectre

Spectre is similar to Meltdown, but instead of attacking proprietary behavior of a chip, it targets previously-unknown weakness of a fundamental CPU design paradigm.
The paradigm, out-of-order execution, uses speculative execution to "guess" what operation should happen next, and do some of that work ahead of time. If the guess is correct, a major speedup is achieved. CPUs with this design are called superscalar processors. Most modern CPUs are superscalar, such as the ones in modern desktops, laptops, and mobile devices.
Spectre takes advantage of superscalar processors by manipulating their speculative branch predictions (guesses). The attacker issues instructions crafted to cause incorrect guesses by the CPU, which permits side-channel analysis. Spectre then uses this information to manipulate what code the CPU executes next, including the private instructions of another running program. This general type of attack is called branch target injection.
Spectre attacks are difficult to implement, because they must specifically target the victim's software. They are also more difficult to prevent, because they affect all superscalar processors, including those created by Intel, AMD, and ARM (Advanced RISC Machine).
The vulnerability is called "Spectre" in reference to speculative processing, and because this problem will "haunt" the computer world for many years to come.
Why are they important?
These vulnerabilities exist in the physical circuitry of the CPU, so they are difficult to fix.
Meltdown affects every Intel CPU created in the last twenty years. Spectre affects a fundamental part of most modern CPUs.
Meltdown attacks can be mitigated by changes to the operating system, which results in slower performance. However, for Spectre attacks, no software-based mitigation may be possible at all.
Is my device affected?
Desktop and laptop computers
Meltdown affects all Intel processors dating back to at least 1995. As of this writing, fixes are in development for Microsoft Windows, macOS X, and Linux operating systems. These fixes mitigate the possibility of attack at the kernel level, at an estimated 5-10% performance cost.
Microsoft Windows users can use the InSpectre tool to show if their computer is protected.
Spectre affects all superscalar processors, which includes the vast majority of consumer CPUs. Scalar processors are not affected. For instance, the Raspberry Pi uses scalar ARM processors, which do not employ speculative processing and are not vulnerable to this attack.
Mobile devices
Android and iOS devices, such as smartphones and tablets, are theoretically susceptible to both attacks. However, the newest versions of Android and iOS include updates to mitigate Meltdown; and Spectre attacks, while possible, were shown to be highly unfeasible.
Web browsers
If you are using Firefox Quantum (version 57 or greater), you are protected from Meltdown when running code, such as JavaScript, in the browser.
Google has announced that Chrome version 64, with an estimated release date of January 23, 2018, will mitigate Meltdown in the browser.
Microsoft Edge users can expect the browser to be patched automatically by Windows Update. Opera has also announced a forthcoming security update to mitigate Meltdown.
How can I protect my device?
To protect your device from the Meltdown attack, install all updates currently available for your operating system.
- For Windows 10, 8, and 7, check for a new Windows Update.
- For macOS X, check for new security updates in the App Store.
- For Android, install the Google December 2017 security update on your smartphone or tablet. You can find updates under Settings, About Device. Newer Pixel, Nexus, and Galaxy phones are immediately eligible for the security upgrade. Check with your manufacturer if you're unsure the update is available for your device.
- For iOS, install iOS 11.2 or higher on your smartphone or tablet. To check for updates, go to Settings, General, Software Update.
